The world's safest
remote access software
*No credit card required

Top 50 IT Management Products 2020

Best Software Reviews Platform
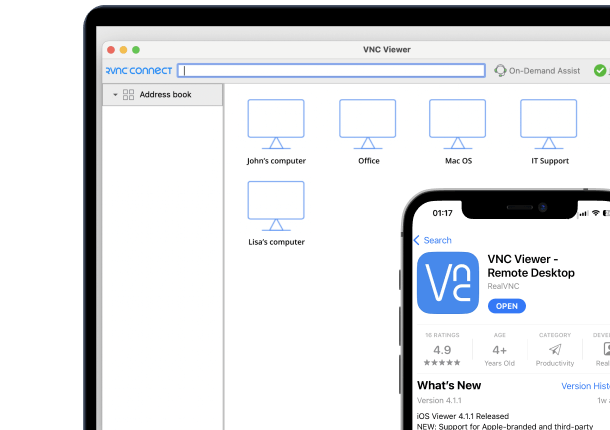
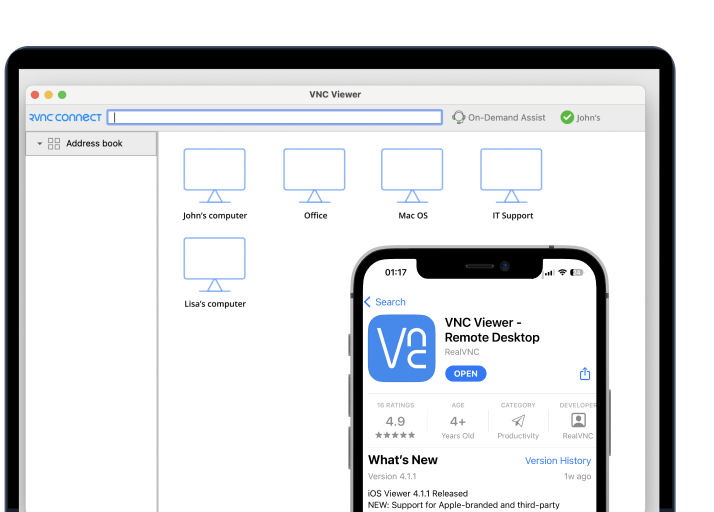



Secure to the core
Keep your systems safe with full session encryption, granular permission controls, and authentication options that ensure complete control of remote access.
Get Started NowA single solution for every device
Simplify your setup and consolidate tools with one solution that works across major desktop and mobile operating systems.
Get Started NowCustomized to your needs
Meet the demands of your business with a highly configurable remote access solution that can be customized to work for you.
Get Started NowFast and reliable connections
Empower everyone with remote access that auto-adjusts to your network speed so your connections are always optimized for the best experience.
Get Started NowOur software is used every day by millions of people worldwide to connect to billions of devices

Michael Balon, IT Manager
Boston Valley Terracotta

Wayne Hobbs, Satellite Control Network Analyst
Telesat Canada

Ben Littleton, Systems and Network Manager
Southern Ohio Medical Center
What are you looking to achieve with RealVNC Connect?
I want to access and manage any
device, from anywhere
I want to offer timely assistance
to teams across my business
Trusted by leading IT teams worldwide
Customer Success Stories

REJI
- Frank Yoder, CEO

Qtrac
Aleks Nikolovski

100.3 FM
James Valentine

MiPi Support
Matt Ireland, Founder

Massage Robotics
*No credit card required